Multi-factor Authentication
OVERVIEW
This article explains how multi-factor authentication (MFA) enhances account security by requiring additional verification after signing in. It covers the setup process for MFA, the three authentication methods Loop supports (push notifications, time-based one-time passwords, and SMS-based authentication), and best practices for keeping accounts secure, including setting up backup MFA methods and protecting credentials.
Use the menu on the left to quickly navigate this article.
What it is
Multi-factor authentication (MFA) is a way of verifying users’ identities by requiring additional validation after signing in. MFA prevents unauthorized access to a user’s account even if their username and password have been compromised.
Why it matters
MFA reduces the likelihood of unauthorized account usage and keeps your data even safer. Usernames and passwords can be stolen in social engineering attacks and data breaches or even programmatically generated in brute force attacks. Requiring an MFA method such as an authenticator app or one-time password greatly reduces the chances of success for bad actors.
How it works
Loop’s MFA works by requiring additional verification information from users upon signing in. After entering a username and password or using single sign-on (SSO), additional proof of identity must be provided before the user can access their account in the Loop admin.
Setup
If MFA hasn’t been set up already, merchants will be prompted to configure an MFA method for their account when they sign in to Loop.
Select an authentication method to use, then follow the setup instructions for that method. For details on each MFA method, see Authentication methods below.
After setting up MFA on their account, the merchant is prompted to verify their identity using their chosen MFA method. Once verification is successful, the merchant is redirected to the Loop admin.
Authentication methods
Loop supports the MFA methods listed below. For troubleshooting information for each method, see Multi-factor Authentication Troubleshooting.
Push notifications
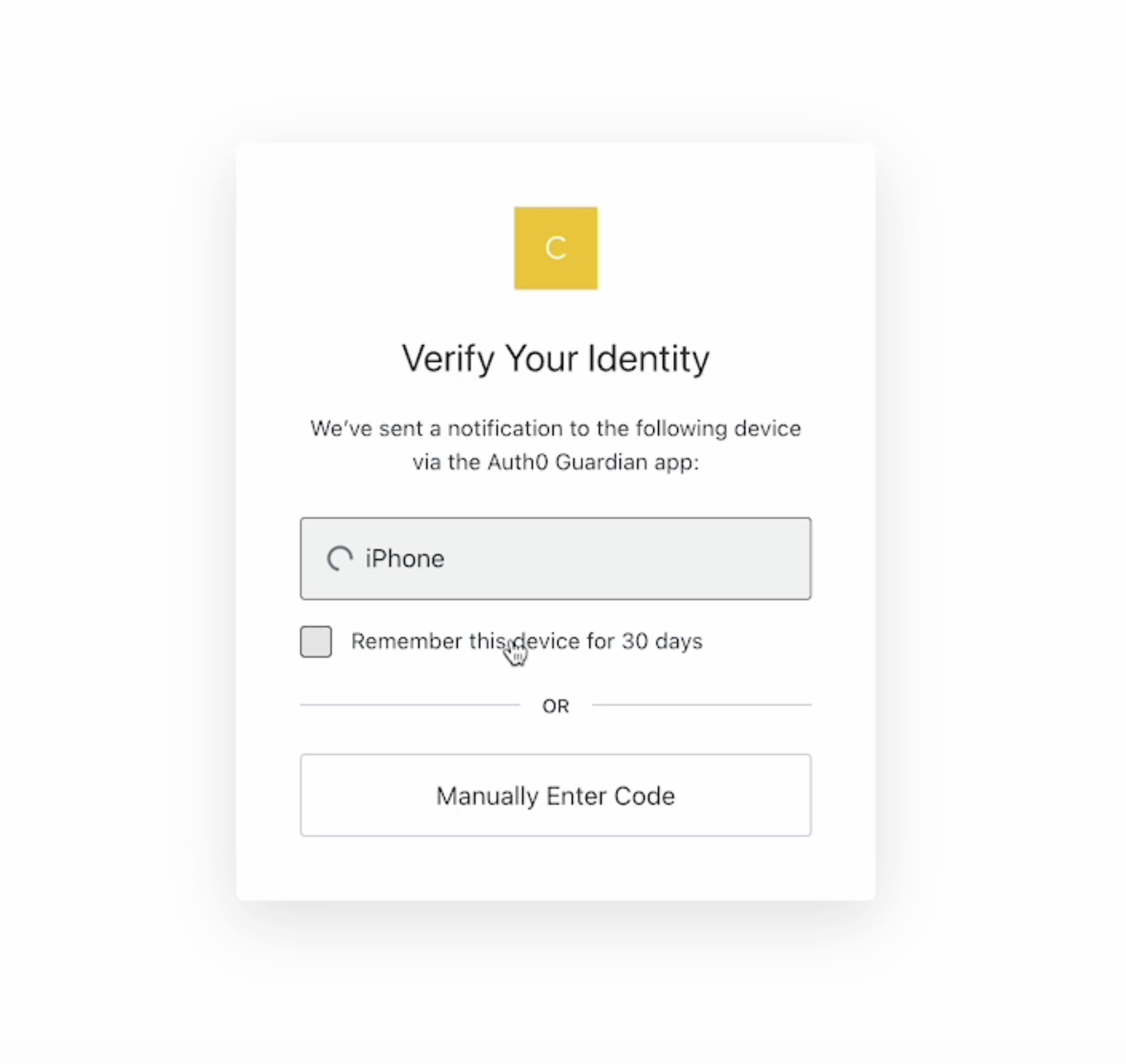
This MFA method sends users push notifications to their pre-registered mobile devices using the Auth0 Guardian app, from which a user can immediately allow or deny access to their account.
Auth0 Guardian can be installed on most Android and iOS devices. For details, see Auth0’s documentation on Auth0 Guardian.
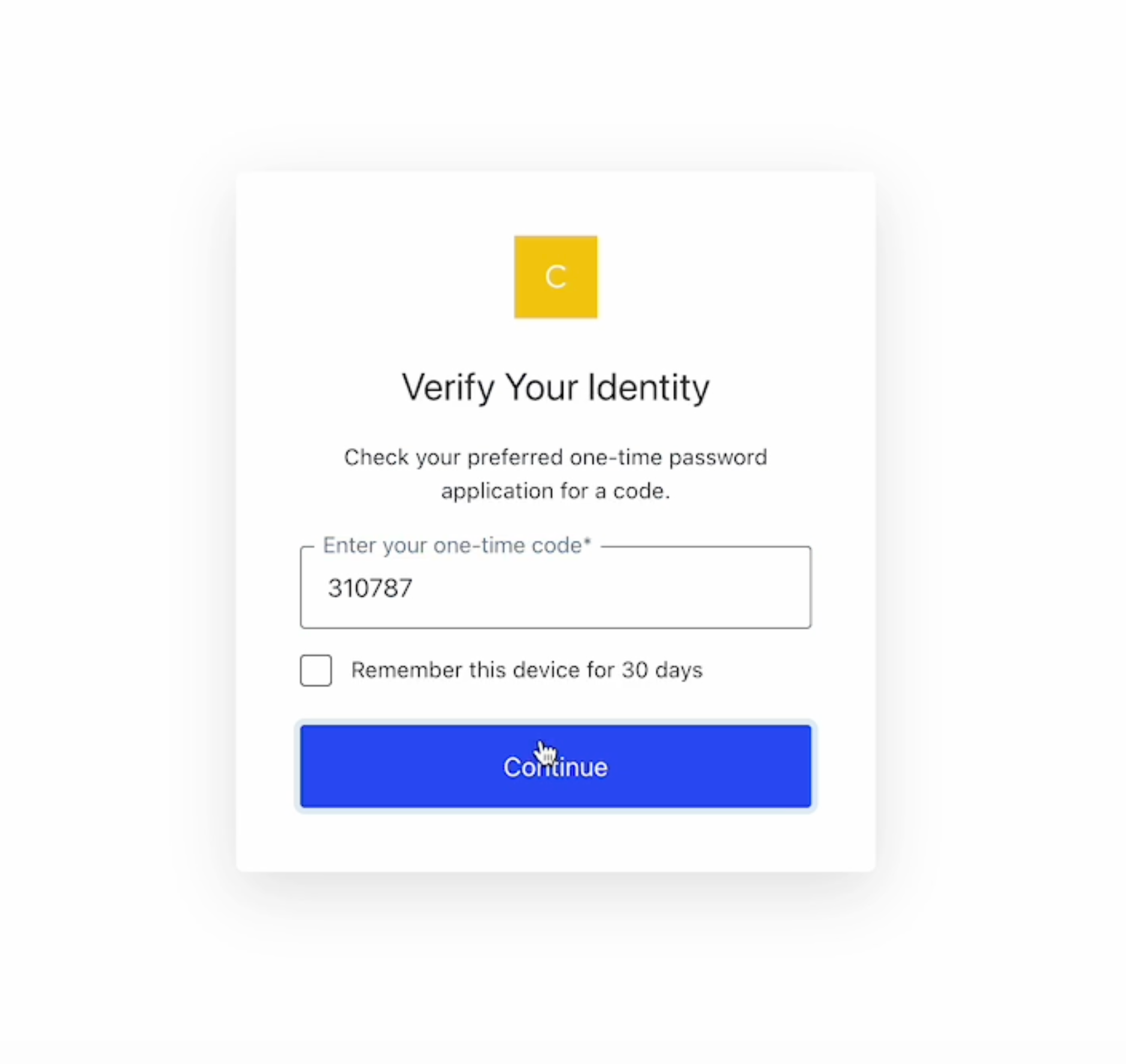
Time-based one-time passwords
Time-based one-time password (TOTP) MFA requires users to enter a time-sensitive numeric password generated on their device to authenticate their account. TOTP tokens are generated in authenticator apps such as Authy or Google Authenticator.
Loop supports the following authenticator apps:
Auth0 Guardian (Google Play / App Store)
Authy (Google Play / App Store)
Google Authenticator (Google Play / App Store)
Microsoft Authenticator (Google Play / App Store)
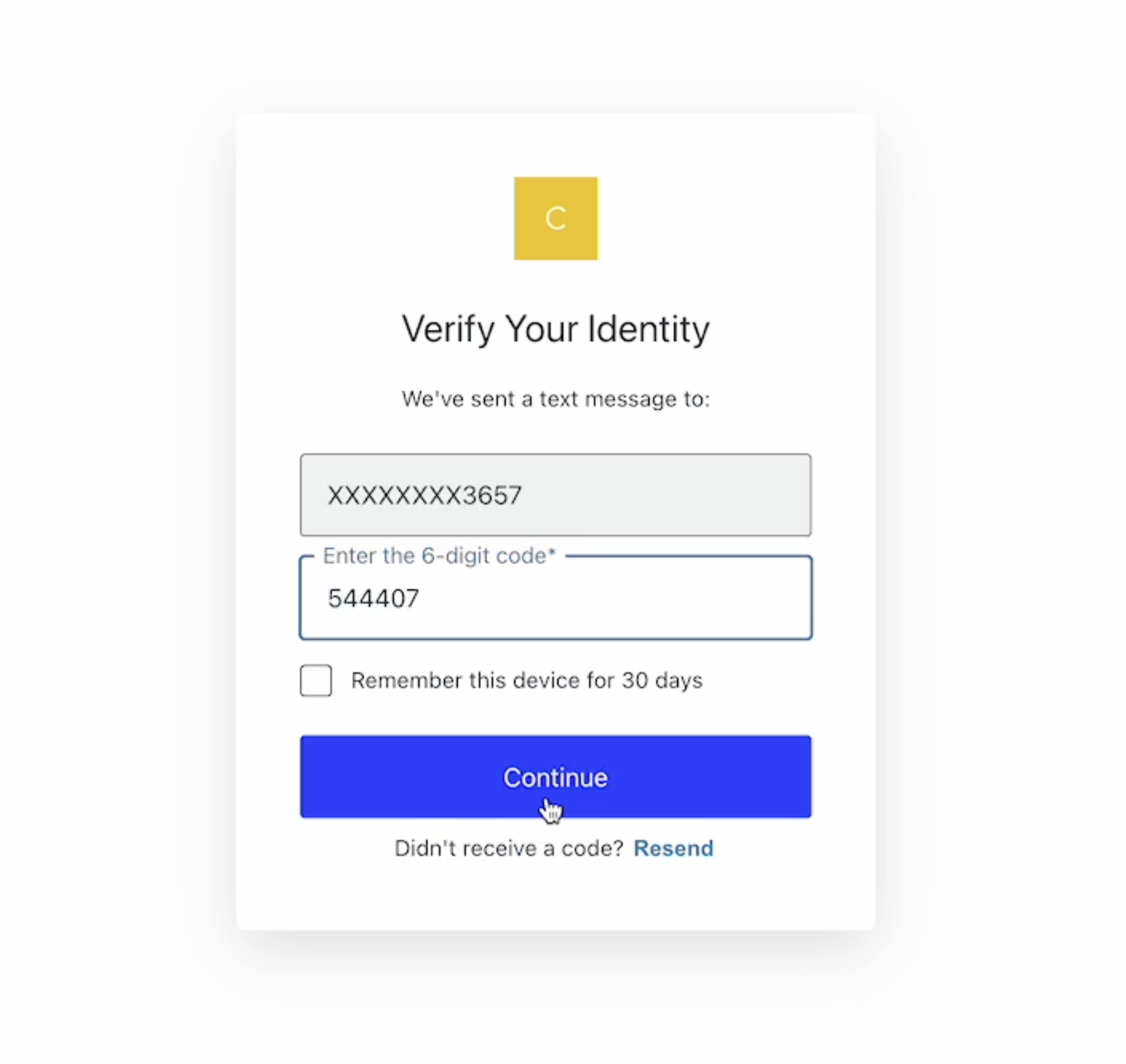
SMS-based authentication
SMS-based MFA allows users to verify their identities with a code that is sent to them by a text message or phone call.
Although still highly effective against preventing unauthorized account access, SMS-based authentication is vulnerable to SIM swapping attacks as well as associated with a higher rate of phishing and social engineering attacks. Loop recommends using the Auth0 Guardian app or TOTP authentication instead if possible.
Best practices
Keep MFA credentials safe and secure. TOTP tokens and SMS authentication codes should be treated like an account password and provided only to Loop. Loop support will never ask for MFA codes.
Set up backup MFA methods. For example, merchants using push notifications as their primary MFA method can set up TOTP authentication as a backup method in case of a poor internet connection.
Be vigilant and report anything suspicious or unusual to Loop’s support team.
Please reach out to support@loopreturns.com with any additional questions.